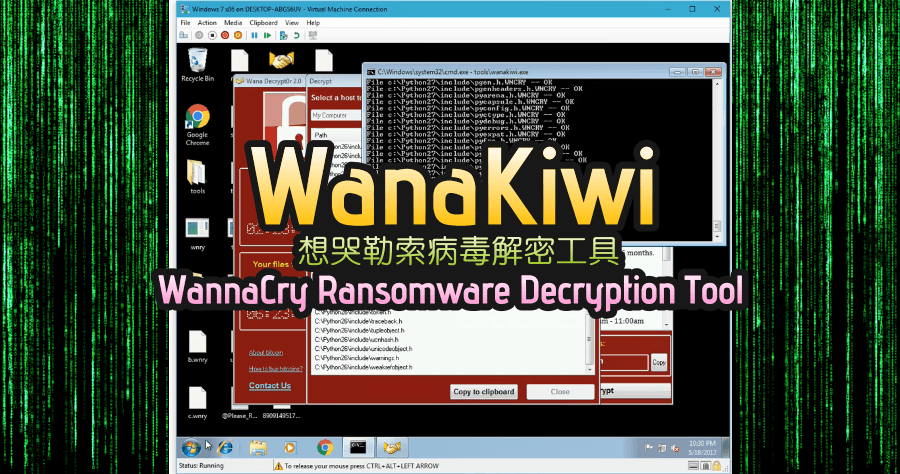
ms17-010 exploit
ThismodulewillexploitSMBwithvulnerabilitiesinMS17-010toachieveawrite-what-whereprimitive.Thiswillthenbeusedtooverwritetheconnection ...,AdetailedwalkthroughofhowtoexploittheEternalBluevulnerabilityonaWindows7Ultimatemachine,coveringbothmanualanda...
Learnmoreaboutthemostdamagingandenduringexploitsintheworld,EternalBlue,andhowtheNationalSecurityAgency(NSA)helpedcreate ...
** 本站引用參考文章部分資訊,基於少量部分引用原則,為了避免造成過多外部連結,保留參考來源資訊而不直接連結,也請見諒 **
此文章參考的來源相關文章推薦
MS17
This module will exploit SMB with vulnerabilities in MS17-010 to achieve a write-what-where primitive. This will then be used to overwrite the connection ...
Exploiting EternalBlue (MS17–010)
A detailed walkthrough of how to exploit the Eternal Blue vulnerability on a Windows 7 Ultimate machine, covering both manual and automated methods.
Microsoft 安全性公告MS17-010
如果攻擊者將特製郵件傳送至Microsoft Server Message Block 1.0 (SMBv1) 伺服器,此安全性更新可解決Microsoft Windows 中與遠端程式代碼執行相關的 ...
Microsoft Security Bulletin MS17-010
This security update resolves vulnerabilities in Microsoft Windows, related to remote code execution if an attacker sends specially crafted ...
MS17-010
Microsoft Security Bulletin MS17-010 was published last March 14, 2017 to address multiple vulnerabilities in Microsoft Server Message Block 1.0 (SMBv1).
MS17-010
The remote Windows host is affected by multiple vulnerabilities. (Nessus Plugin ID 97737)